Our company gained Information Security Management ISO 27001 since 2012, Certifications related to cyber defense industry from the Ministry of Defense (Kementerian Pertahanan Republik Indonesia), and Domestic Component Level (Tingkat Komponen Dalam Negeri/TKDN).
We have handled various projects on national and global scale: Private sector, state-owned enterprises, government, oil and gas, finance, defense and security sectors.

Vision
To be a trusted partner and a leading Cyber Security specialist in South East Asia.
Mission
We are committed to continuously improve the services and innovate new ideas to provide the best solution for our clients.
By investing in and developing our most valuable assets, our staff, we aim to fulfill and exceed our client’s needs.
Assurance of Quality
We aim to always provide services with the highest standard, always in accordance with world class standards of ISO27001 and ISO20000.
Customer Oriented
Our customers are the lifeblood of our business and our most important stakeholder. We strive to meet and exceed their expectations every time.
Self-Improvement
Always striving to provide outstanding products and unsurpassed services that, together, deliver premium value to our customers.
Integrity
Honesty, transparency and commitment to do what’s best for our customers and our company. We openly collaborate in pursuit of the truth.

Industry Leader professionals
The team is made up of competent individuals with years of experience and the team has achieved several cyber security certifications making them as a team of qualified individuals to build and deliver the best solution for cyber security.

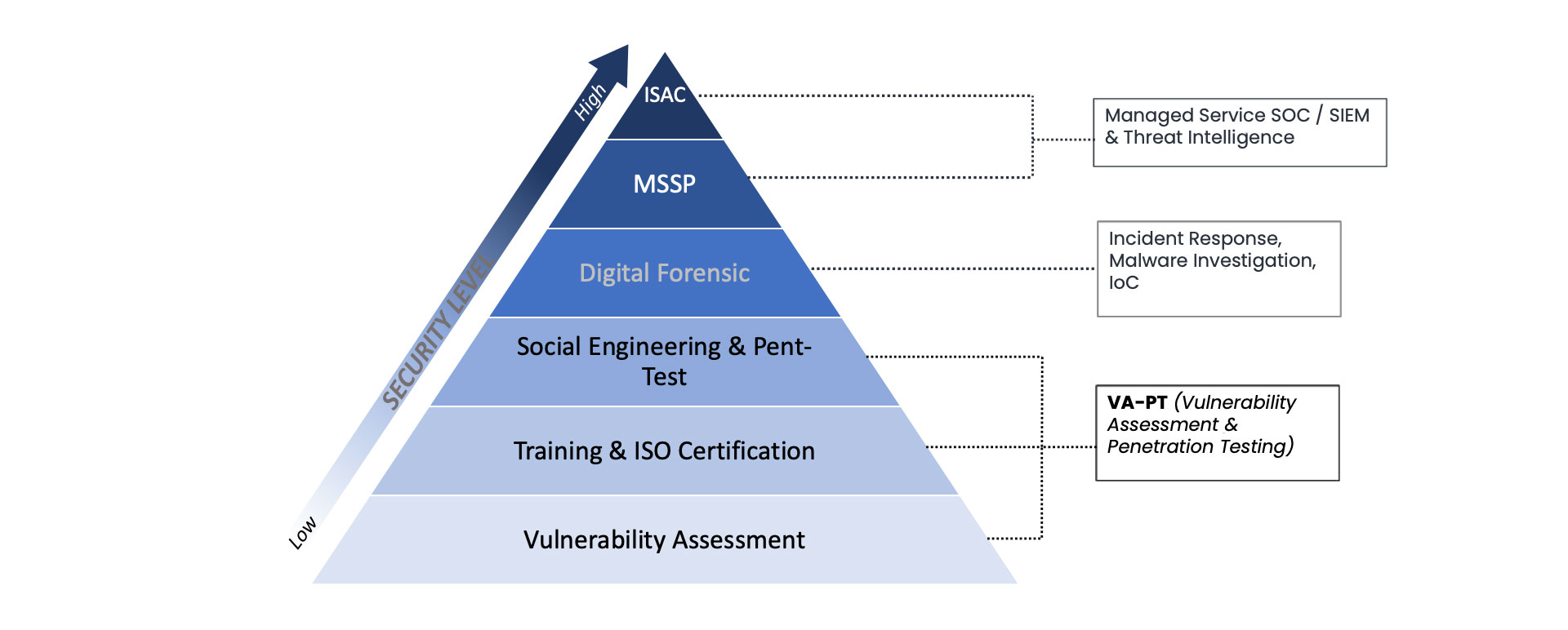
VULNERABILITY ASSESSMENT
the process of discovering, analyzing, and reporting on security flaws and vulnerabilities. Vulnerability scans are conducted via automated vulnerability scanning tools to identify potential risk exposures and attack vectors across an organization’s networks, hardware, software, and systems.


An authorized simulated cyberattack on a computer system performed to evaluate the security of the system
Online & Offline environments | Black, Gray, White Box | Social Engineering | Simulation Brute-force, DDOS, etc | Source code Review | Real case drill.
TOP 10 OWASP
- Broken Access Control
- Cryptographic Failures
- Injection
- Insecure Design
- Security Misconfiguration
- Vulnerable and Outdated Components
- Identification & Authentication Failure
- Software Data Integrity Failure
- Security Login & Monitoring Failure
- Server Site Request Forgery
PTES FRAMEWORK
- Pre – Engagement Interactions
- Intelligence Gathering
- Threat Modelling
- Vulnerability Analysis
- Exploitation of Vulnerabilities
- Post Exploitation
- Reporting
The ‘human-operated’ element means there are skilled and Adaptable financially-motivated people behind these attacks who can Identify and overcome defenses.
Attackers use techniques commonly seen in APT intrusions to gain Access, spread widely over months, and deploy ransomware for maximum impact.

- In order to minimize risks to information security incidents, ISO/IEC 27001:2013 requires management to examine an organization’s information security risks by systematically considering threats, vulnerabilities, and their impacts. For the design and implement coherent and comprehensive information security controls to deal with risks that are deemed unacceptable.
- In addition, the comprehensive adoption of ISO 27001:2013 will ensure information security controls that meet the organization’s information security needs on an ongoing basis.
More and more laws, regulations and contractual requirements are related to information securities and most can be solved by implementing ISO 27001
To prevent security incidents from happening, companies need costs.
While the ISO 27001 investment is much smaller than the cost savings that will be achieved
Get marketing advantage
If the company gets certifications and competitors don’t, then the company will have an advantage in the eyes of customers in maintaining information security and improving IT services
Better organization
ISO 27001 helps resolve situations where employees don’t know what to do because ISO encourages companies to write down the company’s main processes

Teams with special capabilities are tasked with improving the cybersecurity of organizations by preventing, monitoring, detecting, analyzing and responding to security incidents with the help of well-defined technologies and processes/procedures

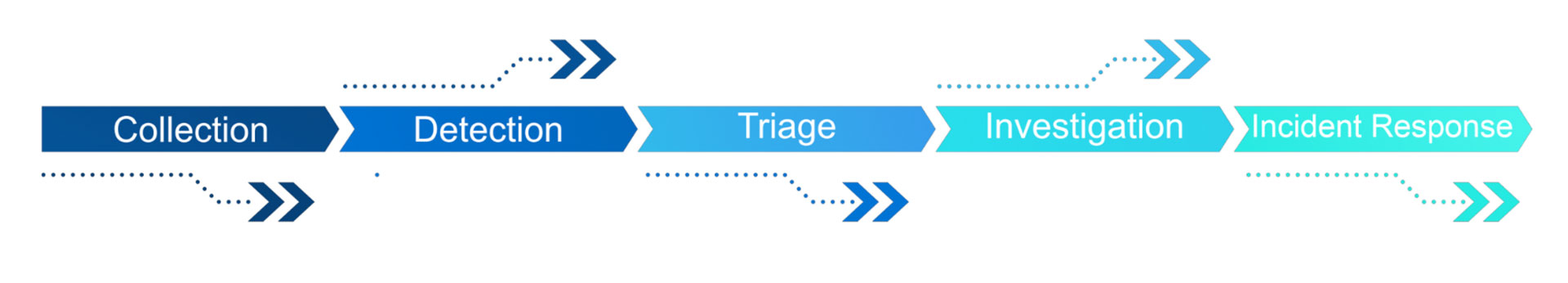

With our expertise and service, we will bring valuable impact and value on :
▪ 24×7 Protection, detection, and response on your business and operation.
▪ Increased productivities
▪ Inspires customer confidence
▪ Defend your customer valuable and data
▪ Efficient on your investment.

Contact information
Praesent mauris nulla, malesuada vitae rhoncus eu, dictum vel lectus. Aenean nec neque lorem. Phasellus in fini bus dictum elit. Phasellus risus nisl, luctus laoreet nibh. Maecenas tincidunt vel libero vel sodales. Proin eu ligula commodo Phasellus risus nisl.







Mon - Thurs: 5am - 10pm,
Friday: 5am - 8pm,
Saturday: 5am - 7pm,
Sunday: 5am - 6pm
We can answer all your questions
Call us: 983-938-938
121 King St, Melbourne VIC 3000, Australia



